Table of Contents
ToggleAs technology advances, it eliminates the distances between regions, connecting the world for communication, collaboration, and subcontracting. Outsourcing is becoming commonplace for enterprises and small businesses seeking diverse services and vendors. Cybersecurity is one of the many domains that are experiencing the benefits of outsourcing, posing a few challenges.
In this blog, we highlight the importance of cybersecurity outsourcing and the key challenges that businesses face while opting for it. To address these challenges, the writing also recommends some strategies that will help firms tackle them. We will also underline the benefits it promises, along with the best practices of outsourcing cyber security with custom development. For those wondering what is cyber security, we start with the basics.
What is Cyber Security?
Cybersecurity is a set of guidelines to safeguard computer systems, networks, and data from unauthorized access, attacks, or damage. It involves implementing measures, including firewalls, encryption protocols, and threat detection, to protect against threats like malware, phishing, and hacking. The aim is to ensure the confidentiality, integrity, and availability of digital information, preventing disruptions and intrusions that could compromise the security of data or systems.
Can Cyber Security Be Outsourced?
Certainly, firms with limited resources can cost-effectively outsource to managed cyber security services. It allows them to onboard seasoned professionals instead of investing in infrastructure and teams. It involves partnering with cyber security companies to handle various aspects like threat detection, incident response, vulnerability assessments, and monitoring. Businesses can access proficient skills, cutting-edge technologies, and round-the-clock control.
Importance of Outsourcing Cyber Security
In the age of digital advancements, undermining the importance of cybersecurity can cost a fortune. As we navigate the complexities of the domain, outsourcing emerges as a strategic imperative. Let’s explore the factors that signify its importance:
1. Persistent Threats
The digital ecosystem is facing extensive cyber threats that continuously evolve to exploit vulnerabilities in systems or networks. From ransomware attacks affecting operations to stealthy phishing schemes deceiving unsuspecting users, the threats are diverse and relentless. In this constant battle, organizations face the daunting task of fortifying their defenses against countless cyber adversaries.
2. Hidden Vulnerabilities
Every piece of software, network, or app contains hidden vulnerabilities that cybercriminals exploit. These vulnerabilities may arise from the coder’s errors, misconfigurations, or out-of-date components. Outsourcing enables organizations to conduct thorough vulnerability assessments, identifying and resolving potential weaknesses before malicious exploitation.
3. Stubborn Bugs
Software bugs, or coding errors, represent a never-ending challenge for organizations, requiring continual testing and improvements. Bugs can serve as entry points for cyber-attacks and even disrupt performance. A cyber security audit includes bug testing, ensuring their systematic detection and patch management to maintain the integrity of digital assets.
4. Menacing Malware
Malicious software, or malware, comes in various forms, including viruses, worms, and trojans that compromise systems or data. A cyber security services company aids in deploying malware detection and prevention mechanisms. This proactive approach helps identify and neutralize malware threats before they infiltrate and wreak havoc on digital infrastructure.
Key Challenges in Outsourcing Cyber Security
Outsourcing cybersecurity has become a common practice for organizations seeking to fortify their defenses against ever-evolving cyber threats. While this strategic approach offers numerous benefits, it also comes with its share of challenges. In this section, we explore the key challenges in outsourcing cybersecurity and strategies to navigate these complexities effectively.
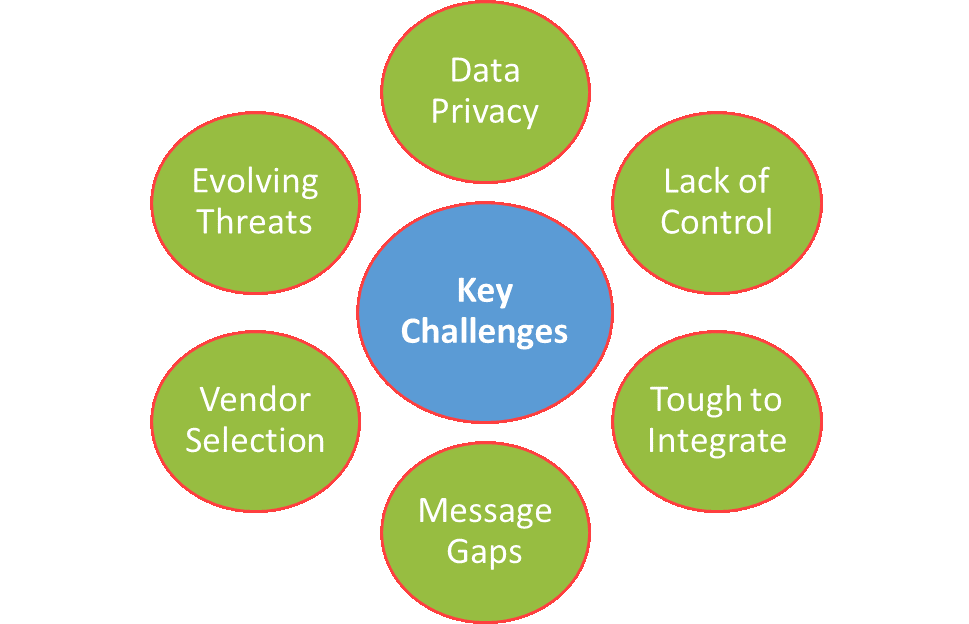
1. Data Privacy Concerns
One of the primary challenges in outsourcing cybersecurity is the handling of sensitive data. Entrusting a third-party provider with access to confidential information poses inherent risks. Organizations must ensure that stringent data privacy measures are in place, aligning with regulatory requirements and industry standards.
Strategy: Conduct thorough due diligence on the cybersecurity provider’s data protection policies, compliance certifications, and track record in handling sensitive information. Clearly define data access and usage protocols within the outsourcing agreement.
2. Lack of Control and Visibility
Outsourcing cybersecurity means relinquishing a degree of control over security operations. This lack of direct oversight can be a concern for organizations, as they may feel less in command of their cybersecurity strategy.
Strategy: Establish clear communication channels and reporting mechanisms with the cybersecurity provider. Regular audits, transparent reporting, and collaboration on incident response plans can help maintain a sense of control and visibility.
3. Integration Challenges
Integrating outsourced cybersecurity seamlessly with existing in-house systems and protocols can be challenging. Misalignments in processes and technologies may create vulnerabilities and hinder the effectiveness of the overall security strategy.
Strategy: Prioritize a thorough understanding of the existing cybersecurity infrastructure. Choose a provider that can seamlessly integrate with current systems and customize solutions based on the organization’s unique needs.
4. Communication Gaps
Effective communication is crucial in cybersecurity, and any gaps in understanding or miscommunication can lead to lapses in security. Differences in language, time zones, or cultural nuances can contribute to misunderstandings.
Strategy: Establish clear communication protocols from the outset. Regular meetings, well-defined reporting structures, and the use of collaboration tools can bridge communication gaps and foster a strong partnership.
5. Vendor Selection
Choosing the right cybersecurity outsourcing partner is a critical decision. With a plethora of providers available, organizations may struggle to identify the most suitable vendor that aligns with their security requirements and business goals.
Strategy: Conduct thorough vendor assessments, considering factors such as expertise, track record, compliance certifications, and scalability. Seek referrals and case studies to gauge the provider’s effectiveness in addressing similar challenges.
6. Evolving Threats
The cybersecurity landscape is in a constant state of flux, with new threats emerging regularly. Outsourcing providers must stay ahead of the curve in adopting the latest technologies and strategies to counter evolving cyber threats.
Strategy: Prioritize cybersecurity providers with a commitment to continuous learning and innovation. Regularly review and update the outsourcing agreement to incorporate emerging threat mitigation strategies.
Benefits of Cybersecurity Outsourcing
There are immense benefits to subcontracting your data and system security projects. We list the most common ones below for your reference to give you an essence of the possibilities.
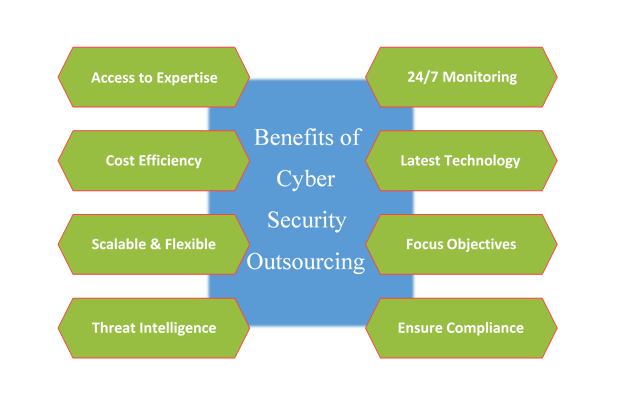
1. Access to Diligent Expertise
One of the foremost advantages of outsourcing cybersecurity is gaining access to a pool of specialized expertise. Cybersecurity service providers employ professionals who are well-versed in the intricacies of cyber threats. They ensure that organizations benefit from their advanced knowledge and experience in handling a diverse range of security challenges.
2. 24/7 Monitoring & Rapid Incident Response
Cyber threats operate around the clock, and so should your cybersecurity defenses. Delegation to vendors aids businesses in continuous monitoring and rapid incident response capabilities. Managed Security Service Providers (MSSPs) can detect anomalies and respond to potential threats in real-time, mitigating the impact of security incidents before they escalate.
3. Cost Efficiency and Resource Optimization
Maintaining an in-house cybersecurity team with the required expertise can be cost-prohibitive for many organizations, especially small and medium-sized enterprises. Subcontracting offers a cost-effective alternative, allowing businesses to leverage comprehensive cybersecurity services without the need for extensive investments in personnel, training, and infrastructure.
4. Access to Cutting-Edge Technologies
The rapidly evolving nature of cyber threats necessitates staying ahead with the latest technologies. Outsourcing cybersecurity services provides companies with access to state-of-the-art security tools and technologies. It ensures that organizations are equipped with the most advanced solutions to counteract emerging threats and vulnerabilities.
5. Scalability & Flexibility
Businesses evolve, and so do their cybersecurity needs. Outsourcing cybersecurity services provides organizations with the flexibility to scale up or down based on their specific requirements. This agility is crucial in adapting to the dynamic nature of cyber threats and implementing security measures that align with the organization’s growth trajectory.
6. Focus on Business Objectives
By subcontracting cybersecurity, organizations can redirect their internal resources and focus on core business objectives. This strategic move allows teams to concentrate on innovation, productivity, and revenue generation, leaving the complexities of maintaining a robust cybersecurity infrastructure to dedicated experts.
7. Comprehensive Threat Intelligence
Hiring cybersecurity agencies often come bundled with access to extensive threat intelligence databases. MSSPs continuously analyze global threat landscapes, providing businesses with valuable insights into emerging risks and vulnerabilities. This proactive approach enables firms to stay ahead of potential threats and implement preemptive measures to mitigate risks.
8. Regulatory Compliance & Risk Management
Navigating the intricate landscape of regulatory compliance is a key component of cybersecurity. Cybersecurity agencies ensure that organizations stay abreast of industry-specific regulations and effectively manage potential risks. Cybersecurity service providers are well-versed in compliance requirements, assisting businesses in implementing measures to meet regulatory standards.
Best Practices of Cybersecurity Outsourcing
Standards and best practices make it easy to outsource your projects to deserving companies. The following best practices would assist you in forming partnerships for subcontracting.
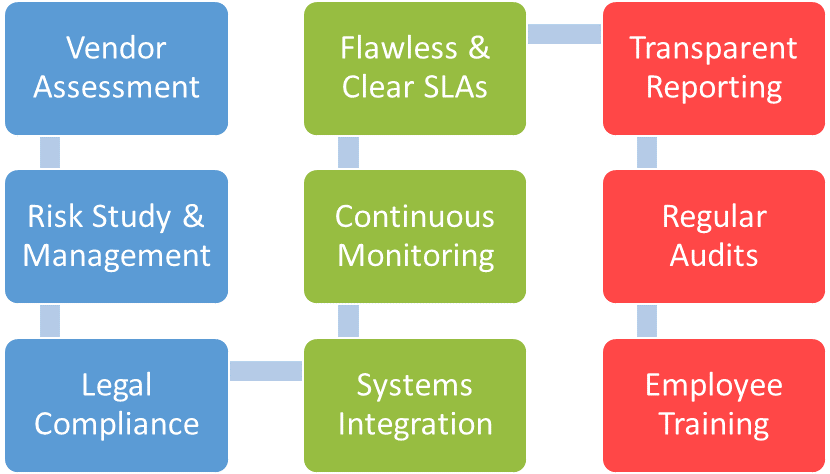
1. Thorough Vendor Assessment
Before entrusting a third party with the critical task of safeguarding your digital assets, conduct a comprehensive assessment of potential cybersecurity vendors. Evaluate their expertise, industry reputation, compliance certifications, and track record in handling similar challenges. Seek references and case studies to gauge the provider’s effectiveness in real-world scenarios.
2. Flawless Service Level Agreements (SLAs)
Establishing clear and measurable Service Level Agreements is essential for setting expectations and holding cybersecurity providers accountable. Clearly outline the scope of services, response times for incidents, and the criteria for success. SLAs should be aligned with your organization’s specific security needs and compliance requirements.
3. Transparent Communication and Reporting
Effective communication is the bedrock of successful cybersecurity outsourcing. Establish transparent channels for communication, regular reporting, and incident response coordination. Ensure that the cybersecurity provider provides detailed reports on security incidents, threat intelligence, and the overall health of your organization’s security posture.
4. Risk Assessment and Management
Conduct thorough risk assessments in collaboration with the outsourcing partner to identify potential vulnerabilities and threats. Establish a risk management framework that prioritizes risks based on their severity and potential impact. Regularly review and update risk assessments to adapt to the evolving threat landscape.
5. Continuous Monitoring and Incident Response
Cyber threats don’t adhere to a schedule, and an effective cybersecurity strategy requires continuous monitoring. Ensure that the outsourcing partner has robust real-time monitoring capabilities. Define clear incident response protocols, conduct regular drills, and collaborate closely to address and mitigate security incidents swiftly.
6. Regular Security Audits and Compliance Checks
Regular security audits and compliance checks are critical to ensuring that the cybersecurity measures are aligned with industry standards and regulations. Work with the outsourcing partner to conduct periodic assessments, penetration testing, and compliance audits to identify and address potential gaps in security.
7. Data Privacy and Legal Compliance
Given the sensitivity of data in cybersecurity operations, it’s crucial to ensure compliance with data privacy laws and regulations. Clearly define data access and usage protocols within the outsourcing agreement. Regularly assess the provider’s data protection measures to align with evolving legal requirements.
8. Integration with In-House Systems
Smooth integration with existing in-house systems and processes is vital for the success of cybersecurity outsourcing. Choose a provider that understands the nuances of your organization’s infrastructure and can seamlessly integrate with your current security protocols.
9. Employee Training and Awareness
Human error remains a significant factor in cybersecurity incidents. Ensure that employees are well informed and trained on cybersecurity best practices. Collaborate with the outsourcing partner to implement ongoing training programs that keep employees vigilant and informed about emerging threats.
10. Regular Review and Improvement
The cybersecurity arena is dynamic, and what works today may need adjustments tomorrow. Regularly review the effectiveness of cybersecurity measures, update protocols based on lessons learned from incidents, and ensure that the outsourcing agreement is flexible enough to adapt to evolving threats and technologies.
Mitigate Risks Through Custom Software Development
Custom software development focuses on the significance of requirements, incorporates best practices, and addresses challenges to reap maximum benefits. It blends the latest tech stack and security measures with industry standards to curate a solution that addresses all concerns. Goal-oriented development embeds client objectives during the development process.
Unique Software Development is a prestigious cyber security managed services provider with expertise in mobile app and web app development. It lists many testimonials and case studies that prove its mark in the trade, making it a perfect choice. If you seek cyber security consulting, tools, or software, contact us for the most impactful cutting-edge cyber security solutions.
Conclusion
Businesses are seeking ways to cut down costs and outsource services from third-party vendors instead of hiring in-house teams. Cybersecurity outsourcing is one such service where they hire expert professionals, optimize resources, scale up, continuously monitor, and ensure compliance. Unique Software Development has a marvelous reputation for handling client projects with value addition and goal-driven development. Hire us as your cyber security consultant and witness the power of cutting-edge custom cyber security software in action.